Computer Science AS
Introduction Information Representation Communications Communications 2 Hardware Logic Circuits Processor Fundamentals Assembly Language Monitor & Control System Software Security, Privacy & Data Integrity Ethics DatabasesAS Practical
Algorithm Data Structures and more Software developmentComputer Science A2
Data Representation File Organisation Advance Logic GatesInternet Virtual Machines System Software Encryption & Security Artificial IntelligenceA2 Practicals
Binary Search Linear Search Bubble Sort Insertion Sort Combined Algorithm Stacks Queues Linked List Binary TreeMore
Reference Pastpaper QuestionsEncryption & Digital Signatures
Encryption is the process of converting a message to a form that can not be understood. We need a key to encrypt the message and a key to decrypt it. The Message before encryption is called the plain text whereas, the message after encryption is the ciphertext/cypher text
Types of Encryption
There are two types of encryption:
- Symmetric Encryption
- Assymetric Encryption
The same key is used to encrypt and decrypt the message. Only the sender and receiver should know the key. The key is usually 256 bits long but the main problem is transferring the key from the sender to the receiver. So if the key is intercepted everything is compromised
A key is used to encrypt the message and a different key is used to decrypt the message. But one key is hidden and the other key is known to the public. The key known to the public is called the public key and the key that is hidden is called the private key
Any key could be used to encrypt the message or decrypt the message but in each condition, it will be different.
In order to verify the source of a message or to make sure the message came from a trusted person, then the sender would use his private key to encrypt the message and the sender's public key is known to everyone and they can decrypt the message and prove it's from that person as the private and public key pair is a match
In order to send a message so it can be read by that person only then we use the reciever's public key to encrypt the message and so only the receiver will be able to decrypt it using their private key
The main problem is verifying whether the private key is actually the senders. We can prove the public key matches with the private key but how do we know that the private key is some else pretending to be the sender
To illustrate this point, let's consider a website that is pretending to be Apple.com. You will be able to communicate with them but you can't authenticate them. So to get around this we need a digital certificate
Digital Certificate
A Digital Certificate is not an actual hardcopy certificate. It is a certificate that holds the details of the owner's public key that is verified by a trusted 3rd party called the CA.
The Below diagram explains how a digital certificate is made
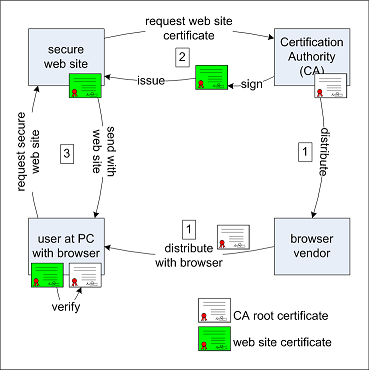
1. First, the details of the owner and his public key are given to the CA
2. The CA will verify the owner that requested the digital certificate using the National Card
3. The CA will encrypt the holder's public key using the CA's private key to form the digital signature
4. The digital certificate is sent to the holder and he puts it on his or her website
5. When a person views this website, he accesses the certificate and uses the trusted CA's public key to decrypt the digital signature to get the websites public key to start communicating
What is in a DIgital Certificate?
This came in a past paper so I will just tell you the points:
1. Serial Number
2. Owner's Public key and details
3. CA's digital signature
4. Hashing Algorithm
Digital Signature
What's the difference between a digital signature and a digital certificate?
Digital Signature is the encrypted hashed message
Message Digest is the hashed message
Now another thing that is important in security is duplication or making sure that the message is not altered. In this case, we need the idea of a message digest. Below shows the steps of transferring data
1. Data is hashed to form the message digest. A Hashing algorithm makes sure the message is converted to a fixed length of data
2. The message digest is encrypted using the sender's private key and this is the digital signature formed
3. The Hashing Algorithm is sent also
4. The Digital Signature is received and decrypted using the sender's public key to get the message digest. The message digest could be used to get the actual message.
5. The actual message is hashed using the hashing algorithm again to form the message digest
6. The two message digests are compared to see if they match. If they match then, the message is not altered
Understand that we use the message digest to prove that the message is unaltered
Types of Symmetric Encryption
There are many methods of generating a key for symmetric encryption and that is by using permutation and shifting. This is not required for you to know! If the Key is made available only to both parties then it is impossible to break by the brute force method. For example, a 256 bit Key will take 2256 tries. The brute force method is the process of trying all possible combination in order to get the correct key
SSL & TLS
SSL Stands for Secure Socket Layer and TLS stands for Transport Layer Security
TLS is the new advance version of SSL.
SSL is the layer that enables safe transmission of data across the HTTP protocol, that's why you see your HTTPS (secure) which is more secure. It encrypts data so it is usually used for online banking and online eCommerce sites and for secure file and mail transfer
It is necessary for you to mention the word secure
TLS has advance security such as session caching and enhanced encryption. This means the session key only is available for a short period.
We will talk about the steps of the SSL protocol:
1. A request is sent to the website by the client for the digital certificate and SSL certificate
2. If the client or browser is able to verify then a request is sent to the website using the website public key to start transmission.
3. If the website accepts it then it sends an acknowledgment with the session key
4. The client uses the session key to start communication that is highly secure
Quantum Cryptography
These use light through special medium or wires such as fiber optics to encrypt messages
Yous don't have to read this paragraph as it is a highly advance explanation
In Quantum cryptography, light signals are sent at different polarisations of light. We know light waves are transverse waves that vibrate perpendicular to the energy of the way and it is clear that in most diagrams, the waves vibrate up and down but, actually in the 3d world, they can vibrate horizontally or even diagonally. According, to Heisenberg's Uncertainty principle, the exact position and momentum of a wave or particle can not be known due to the wave-particle duality. which means if a hacker tries to intercept the fiber optics and tries to measure the polarisation of the light he himself destroys the message and does not allow it to pass. The idea is that the act of measuring can cause data to be destroyed
The basic idea is that the polarisation of the light is hard to determine without destroying the message itself and so it is highly secure
1. It is non-repudiation or can not be altered
2. More secure or harder to tap
3. Can be used to send longer keys
Quantum Cryptography is used heavily in the symmetric encryption process and is used mainly to transfer the key for symmetric encryption. I will explain how this key is transferred and is considered to a be secret code
Explanation of Quantum Cryptography
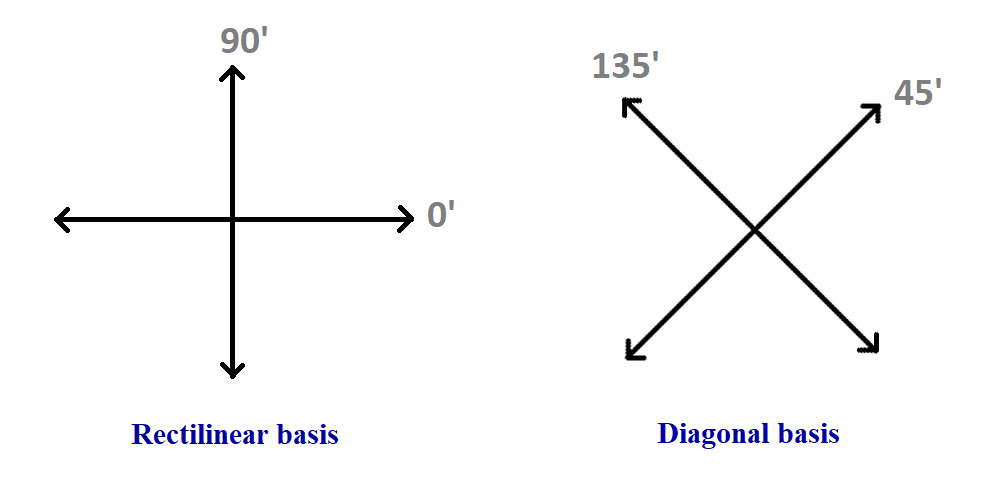
Both the receiver and sender decide the value for the polarisation of lightwaves. For example, Up & Left are 1 and Diagonals are 0. The tricky part is that this is not fixed and this is done randomly. For example, one bit could be 0 for diagonal and another bit could be 1 for diagonal again. The assigning process is done randomly by the sender. Then the sender sends the polarised light (that was randomly generated and corresponds to each bit) and also the receiver assigns randomly the polarisation basis for each bit POSITION at the receiver's end. Now according to probability, there is a chance that some are going to match. Then the sender will tell the receiver the basis of his polarised value for each bit POSITION to the sender and the reciever will see which ones are matched and tell the sender the position where they match. The Polarisation where they match is the bits used. This somehow creates a secret code (the key) between them only
Let me put it in an easy illustration of the similar concept. Say the sender randomly generates 24 bit keys in a specified order only known to the sender
0110 0001 0111 ... Random order
Say the sender also randomly generates
0111 0110 0001 ... Random order
The receiver sends his set of 24 keys and the sender compares it and tells which position matches. If this was done using quantum cryptography then the hacker can't read what is sent and they don't know the position that matches. In some cases, there can be no matches but this is unlikely
Likewise, in actual cryptography, polarisations of light are sent randomly and are assigned with 1 or 0 and the places where they match are sent
